We appreciate you inquiring about our Google Integration scopes. Like us, you take security seriously! So, let’s breakdown our required access to Google Calendar, how it works, and how we keep your personal information secure.
As of June 2023, our exploringnotboring.com platform is in BETA. This allows us to gather meaningful feedback, test, and finesse and finalize our features. During this time, our Dev Team is in the process of verifying our app with Google to finalize our Google Calendar integration for Partners & Seekers.
Sooooo, that means you’ll see this unsettling little warning! 😱
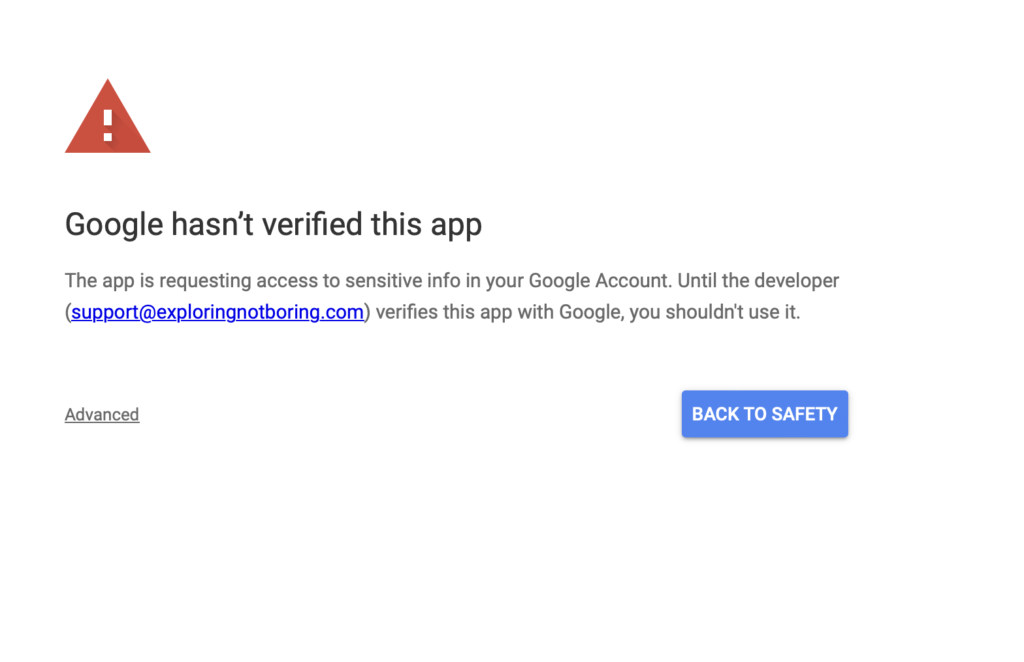
But don’t worry, we’re not hobgoblins!
Google shows this warning as a protection for its users, informing them if an app requires important permissions such as READ & WRITE and is unverified.
If you trust the app, just click Advanced to continue.
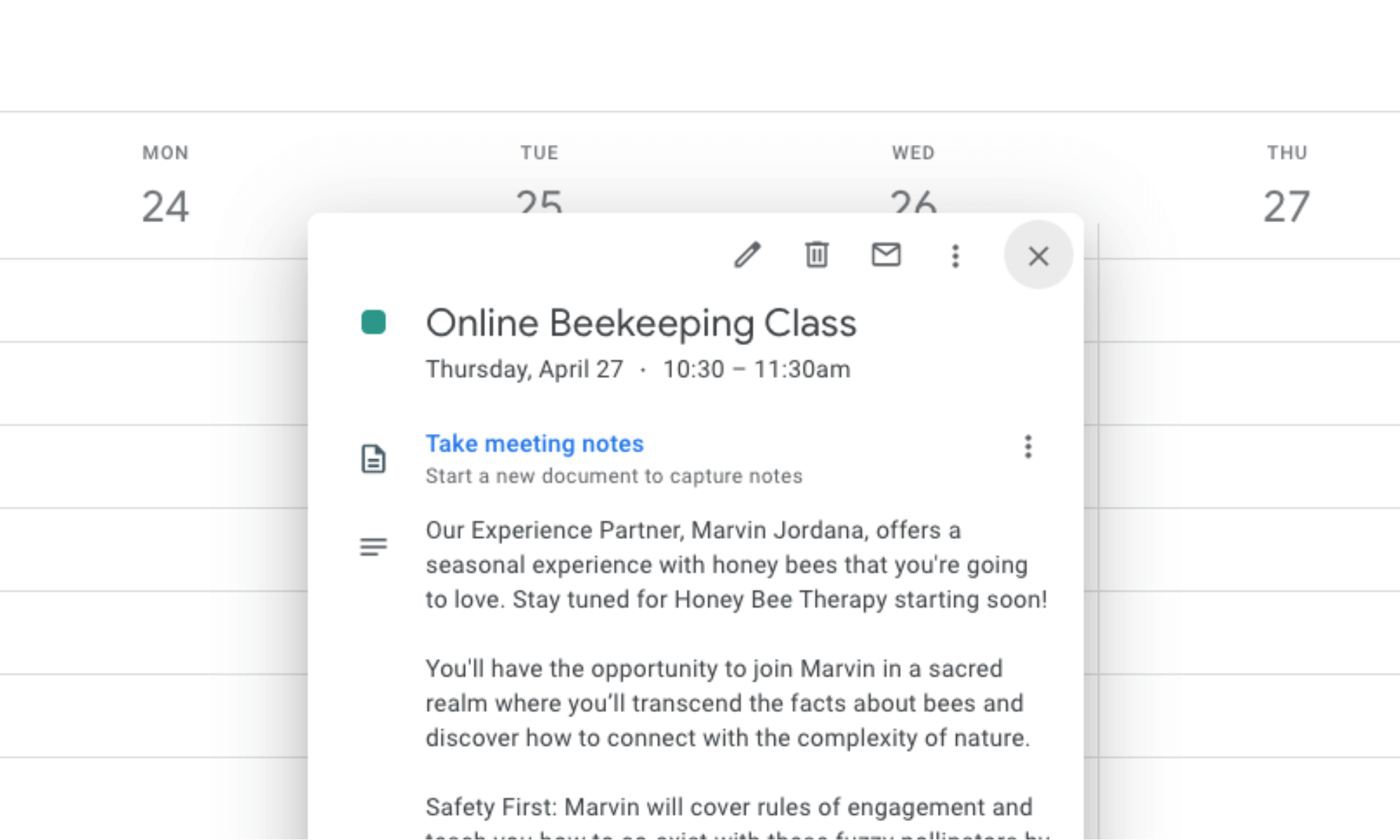
Google Verification is Required
Since we require READ & WRITE scopes, Google verification is required.
These scopes are necessary for us to complete important functions such as the ability to automatically create meeting links and edit or delete ENB Events (WRITE), and consult the calendar (READ) for real-time availability.
Some permissions have been requested in advance for upcoming features such as Resource Management, voiding availability, automatically adding events to your calendar, and allowing the ability to reschedule.
But you might be thinking, “That’s cool, I’m good with it, but why do you need access to ALL my calendars? I’m not comfortable with that level of access.”
Understood! Here’s why:
Google’s Default Access to All Calendars
The information that you see in the screenshot below is the default access by Google when granting access to the Calendar.
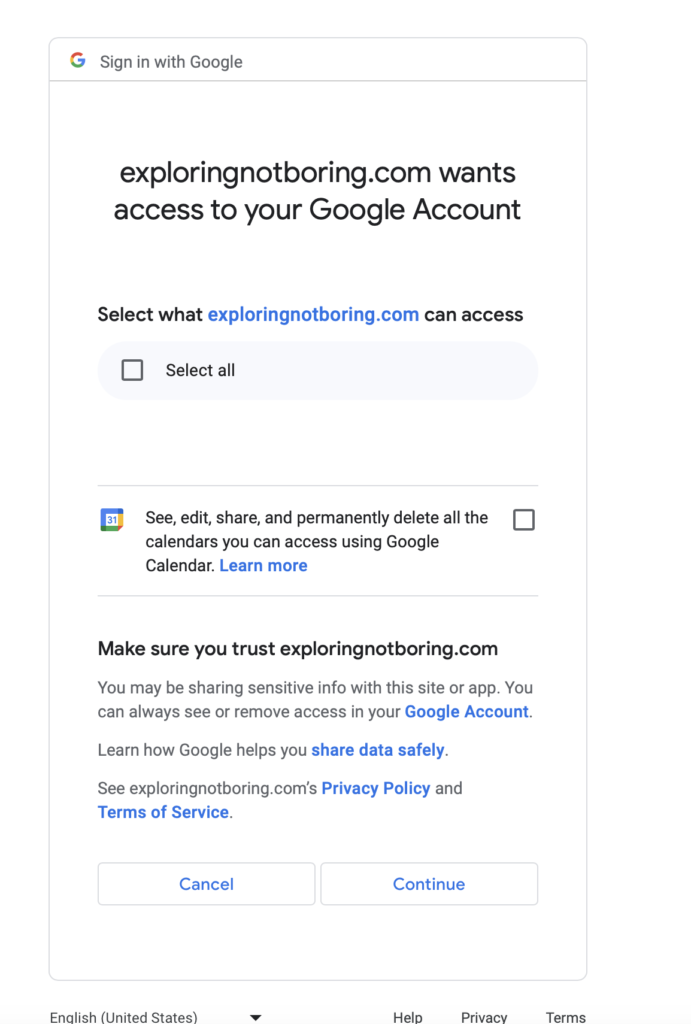
Whenever you’re connecting your Google Calendar to an app, you’re granting Google’s default access to all calendars. Here’s an example from Calendly:
Then sometimes the app may build a feature to allow you to refine the calendar you want to use, like Calendly does in the example below, and like ENB will do for our Resource Management feature coming soon:
The scopes specified to Google for their technical support to know what actions we will do with the default scopes and which ones we will use, are:
- See the title, description, default time zone, and other properties
- See, create, change, and delete events on Google calendars you own
Since access to all calendars is the Google default, we cannot adjust the integration to be more specific. Though that is a good idea!
That said, our web app will only WRITE to events that we create. Meaning, we will only edit or delete events created by our platform, so no worries there!
Hopefully, this clarity has resolved or damped your concerns enough to move forward with peace of mind.
If you do not feel comfortable granting permission to our app at this time, that’s okay. We can update you once our Google integration is verified. Just let us know below.
Alternative Options for Google Calendar Access
You can opt to only use the Zoom integration for your Online Experiences. This will skip Google Calendar Access altogether, while still generating your link.
Of course, we highly recommend using our Google integration to make your life easier by leveraging automation for calendar events.
Especially, as we release super cool new features, such as Resource Management, which will help you maximize your bookings across multiple experiences and manage your real-time availability from your calendar by allowing you to void days or time slots.
So, How Do We Secure Your Personal Data?
This article breaks down some of our security measures to help give you peace of mind. The article is directed toward card data, but it encompasses security protocols that help secure our entire site, integrations, and User data, such as TLS, HTTPS, AES-256 encryption (Advanced Encryption Standard with a 256-bit key), and up-to-date code libraries to eliminate vulnerabilities.
If you still have questions or concerns, please don’t hesitate to reach out. We’re happy to help!
Need more help?
Try these steps:

Search the Help Hub
Find the answers you need!

Contact Us
We’ll help you get there!







0 Comments